The following process will help you remove it from your system easily and safely.
Worm.Win32.Netsky Manual Removal Process:
1. Click on the Start Menu button, then click on the Control Panel option, and then Double-click on the Add or Remove Programs icon.
2. Locate Worm.Win32.Netsky and double-click on it to uninstall Worm.Win32.Netsky. Follow the screen step-by-step screen instructions to complete uninstallation of Worm.Win32.Netsky.
3. Restart the computer.
4. When it has completed uninstalling you can close Add or Remove Programs and your Control Panel.
5. Close all programs.
6. Stop Worm.Win32.Netsky process. If you do not know how to stop a running process, click here to read more.
7. Delete the following infected files from your system.
EasyAV.exe
EasyAV
secound_document4.pif
e-mail3.pif
approved_file7.pif
Remove Worm.Win32.Netsky with SmithfraudFix:
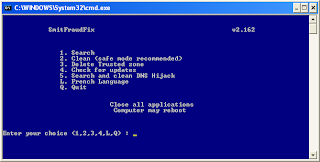
1. Download SmithfraudFix tool and save it to your desktop.
2. Reboot your computer in Safe Mode (before the Windows icon appears, tap the F8 key continually)
3. Double-click SmitfraudFix.exe
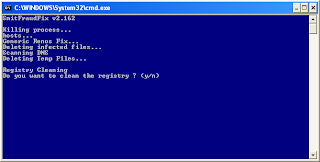
4 Select 2 and hit Enter to delete infect files.
5. You will be prompted: Do you want to clean the registry ? answer Y (yes) and hit Enter in order to remove the Desktop background and clean registry keys associated with the infection.
6. The tool will now check if wininet.dll is infected. You may be prompted to replace the infected file (if found): Replace infected file ? answer Y (yes) and hit Enter to restore a clean file.
7. A reboot may be needed to finish the cleaning process. The report can be found at the root of the system drive, usually at C:\rapport.txt
Restore Trusted and Restricted site zone
1. To restore Trusted and Restricted site zone, select 3 and hit Enter.
2. You will be prompted: Restore Trusted Zone ? answer Y (yes) and hit Enter to delete trusted zone.
Search
1. Select 1 and hit Enter to create a report of the infected files. The report can be found at the root of the system drive, usually at C:\rapport.tx
(Disclaimers: These instructions are free and not guaranteed to work. Please use it at your own risks. We are not responsible for any damages.)
