Wednesday, November 12, 2008
Google Chrome Shortcuts
Friday, October 24, 2008
How to Enable/Disable Auto Paly in Removable Drive
You will see the Group Policy window. You should select Administrative Templates \ System in the tree view:
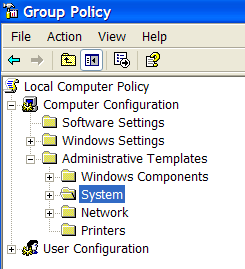
You will see an item "Turn off Autoplay"
Double click the item, and set the radio button to Enabled, and change the "Turn off Autoplay on" to All Drives.
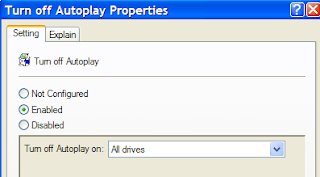
Always Disable AutoRun property for all drive, it will reduce virus attack from removable media
Tuesday, October 21, 2008
AVG Anti-Virus 8.0 Virus Definition Update Error
When updating AVG 8.0 virus definition
Receiving an error "Invalid Update Control CTF File".
Solution:
You need to remove the .CTF temp files in C:\Documents and Settings\All Users\Application Data\Avg8\update\download…. Dont delete all the .bin files in there unless you want to re-run all updates since your original installation. Only remove the avginfo files that end with .ctf.
There were two .CTF files (avginfoavi.ctf and avginfowin.ctf) in that folder.
Note: The Application Data folder is hidden by default. You need to enable Windows Explorer to show hidden files in order to view the Application Data folder. Alternately, type the above folder path in the Start, Run dialog and press {ENTER} to launch the folder.
Monday, September 29, 2008
How to get more traffic
If your have a new web site or new blog, or your blog having low click rate..
log on to any traffic exchange click and earn credit and convert your credit into your web site traffic,

check your web traffic from google analytics .
Wednesday, September 17, 2008
LInux Keyboard shortcuts ( Gnome & KDE )
FOR GNOME
General Shortcut Keys
--------------------------------------------------------
Alt + F1 - Opens the Applicantions Menu .
Alt + F2 - Displays the Run Application dialog.
Print Screen - Takes a screenshot.
Alt + Print Screen - Takes a screenshot of the window that has focus.
Ctrl + Alt + right arrow - Switches to the workspace to the right of the current workspace.
Ctrl + Alt + left arrow - Switches to the workspace to the left of the current workspace.
Ctrl + Alt + up arrow - Switches to the workspace above the current workspace.
Ctrl + Alt + down arrow - Switches to the workspace below the current workspace.
Ctrl + Alt + d - Minimizes all windows, and gives focus to the desktop.
F1 - Starts the online help browser, and displays appropriate online Help.
Window Shortcut Keys
--------------------------------------
Alt + Tab - Switches between windows. When you use these shortcut keys, a list of windows that you can select is displayed. Release the keys to select a window.
Alt + Esc - Switches between windows in reverse order. Release the keys to select a window.
F10 - Opens the first menu on the left side of the menubar.
Alt + spacebar - Opens the Window Menu .
Arrow keys - Moves the focus between items in a menu.
Return - Chooses a menu item.
Esc - Closes an open menu.
Ctrl + Alt + right arrow - Switches to the workspace to the right of the current workspace.
Ctrl + Alt + left arrow - Switches to the workspace to the left of the current workspace.
Ctrl + Alt + up arrow - Switches to the workspace above the current workspace.
Ctrl + Alt + down arrow - Switches to the workspace below the current workspace.
Ctrl + Alt + d - Minimizes all windows, and gives focus to the desktop.
Panel Shortcut Keys
----------------------------------
Ctrl + Alt + Tab - Switches the focus between the panels and the desktop. When you use these shortcut keys, a list of items that you can select is displayed. Release the keys to select an item.
Ctrl + Alt + Esc - Switches the focus between the panels and the desktop. Release the keys to select an item.
Ctrl + F10 - Opens the popup menu for the selected panel.
Tab - Switches the focus between objects on a panel.
Return - Chooses the selected panel object or menu item.
Shift + F10 - Opens the popup menu for the selected panel object.
Arrow keys - Moves the focus between items in a menu. Moves the focus between interface items in an applet also.
Esc - Closes an open menu.
F10 - Opens the Applications menu from the Menu Bar , if the Menu Bar is in a panel.
Application Shortcut Keys
-------------------------------------
Command
Ctrl + N New
Ctrl + X Cut
Ctrl + C Copy
Ctrl + V Paste
Ctrl + Z Undo
Ctrl + S Save
Ctrl + Q Quit
FOR KDE
| Alt-F2 | Execute Command |
| Ctrl - B | Add Bookmark |
| Ctrl-Esc | List of running applications. |
| Ctrl - W | Close |
| Alt-Tab | Switch forward among windows |
| Ctrl - C | Copy |
| Alt-Shift-Tab | Switch backward among windows |
| Ctrl - End | End |
| Ctrl - F1 to F12 | Switch to Desktop 1 - 12 |
| Ctrl - F | Find |
| Shift-Ctrl-F1 to F4 | Switch to Desktop 13 to 16 |
| F3 | Find Next |
| Ctrl-Alt-Esc | Kill Window (Click on the window to action the kill.) |
| Ctrl - F3 | Find Prev |
| Ctrl-Alt-Delete | Logout (To complete logout process, Tab & Enter) |
| F1 | Help |
| F12 | Toggle cursor key mouse emulation |
| Ctrl - Home | Home |
| Alt - F1 | Popup KDE launch menu |
| Ctrl - Insert | Insert |
| Ctrl-Tab | Switch forward one desktop |
| Ctrl - N | New |
| Ctrl-Shift-Tab | Switch back one desktop |
| Ctrl - Down | Next Complete Match |
| Alt - F4 | Window close |
| Down | Next Item in List |
| Alt - F3 | Window open menu |
| Ctrl - O | Open |
| Ctrl - V | Paste |
| "Windows" Menu | Popup Menu Context |
| Ctrl - Up | Previous Complete Match |
| Up | Previous Item in list |
| Ctrl - P | |
| Page Up | Prior |
| Ctrl - Q | Quit |
| Ctrl-Shift-Z | Redo |
| F5 | Reload |
| Ctrl - R | Replace |
| Ctrl - S | Save |
| Ctrl - A | Select All |
| Ctrl - E | Text Completion |
| Ctrl - Z | Undo |
| Shift - F1 | What's this |
| Ctrl - Plus (+) | Zoom In |
| Ctrl - Minus (-) | Zoom Out |
Saturday, September 6, 2008
How to rate your browser
benchmark your favorite browser by acid test
Acid1 Test
---------------------
Acid1 is a test page for web browsers. It was developed in 1998 and was important in establishing baseline
interoperability between early web browsers, especially for the CSS1 specification.

http://www.w3.org/Style/CSS/Test/CSS1/current/test5526c.htm
Acid1 Test 100% success screen shot
Acid2 Test
-----------------------
Acid2 is a test page published and promoted by the Web Standards Project to identify web page rendering
flaws in web browsers and other applications that render HTML. It was developed in the spirit of Acid1,
a relatively narrow test of compliance with the Cascading Style Sheets (CSS) standard

http://acid2.acidtests.org/
Acid2 Test 100% success screen shot
Acid3 Test
-----------------------
Acid3 is a test page from the Web Standards Project that checks how well a web browser follows certain web standards,
especially relating to the DOM and JavaScript.

http://acid3.acidtests.org/
Acid3 Test 100% success screen shot
Friday, September 5, 2008
Online File Scan - Free Virus Detection
If you have a suspicious file, submit it online . Find the threat behind it, the service is free,
Following antivirus are used for scanning your file
AhnLabV3, AntiVir, Authentium, Avast, AVG, BitDefender, CATQuickHeal,
ClamAV, DrWeb, eSafe, eTrustVet, Ewido, FProt, Fortinet, GData, Ikarus, K7AntiVirus,
Kaspersky, McAfee, MicrosoftNOD32v2, Norman, Panda, PCTools, Rising, Sophos, Sunbelt,
Symantec, TheHacker, TrendMicro, VBA32, ViRobot, VirusBuster, WebwasherGateway, etc etc
Tuesday, September 2, 2008
Make your Online Money Transactions secure
- Use only your personal computer for (e)banking [ never use public computers ]
- Create a new account in your operating system for banking purpose
- Protect your system with anti virus and firewall
- Clean your cookies, cache etc before login to your bank account
- don't open any third party software while your are logged in your bank account
- don't browse any unknown or public sites while your are logged in your bank account
- Use any safe browsing software like ForeceField
- Clear cache and cookies before shutting down the system
Friday, August 22, 2008
How to Make Money Online
get paid to click on ads and visit websites
The process is easy! You simply click a link and view a website for few seconds to earn money. You can earn even more by referring friends. You'll get paid for each website you personally view and each website your referrals view. Payment requests can be made every day and are processed through Payment site.
Earnings Example
» You click 10 ads per day ~ $0.10
» 20 referrals click 10 ads per day ~ $2.00
» Your daily earnings ~ $2.10
» Your weekly earnings ~ $14.70
» Your monthly earnings ~ $63.00
The above example is based only on 20 referrals and 10 daily clicks. Some days you will have more clicks available, some days you will have less. most of the PTC site have ads in bet
you can also buy un reffered users to your refference list
MONEY MAKING SYTES ...
 Recommended ( more secure and innovative }
Recommended ( more secure and innovative }
Tuesday, August 12, 2008
How to remove Virus from USB Drives
go to "Tool >> Folder Option >> View" click on "Show hidden files and folders" and uncheck the "Hide Protected operating system files "
click apply and ok.
If autorun virus exists, drive will contain a "autorun.inf" file. right click and open it in "Notepad".(DONT DOUBLE CLICK ON AUTORUN.INF).
in that file u can find a entry like,
"[autorun]
open = CDstart.exe" and some extra fields
Locate the executable (exe) file and delete it, and delete the "autorun.inf" file also.
Your USB Drive is Now Virus Free ( Autorun Virus).
if you get any Error message from the Explore while deleting the file, then the virus is infected on your computer also.
if you can detect the virus file in your pc then kill the process and delete the file and repeat the above steps. Otherwise use any antivirus to remove it.
Make Firefox Faster and Fix Memory problems
1. Type “about:config” into the address bar and hit return. Scroll down and look for the following entries:
network.http.pipelining network.http.proxy.pipelining network.http.pipelining.maxrequests
Normally the browser will make one request to a web page at a time. When you enable pipelining it will make several at once, which really speeds up page loading.
2. Alter the entries as follows:
Set “network.http.pipelining” to “true”
Set “network.http.proxy.pipelining” to “true”
Set “network.http.pipelining.maxrequests” to some number like 30. This means it will make 30 requests at once.
3. Lastly right-click anywhere and select New-> Integer. Name it “nglayout.initialpaint.delay” and set its value to “0″. This value is the amount of time the browser waits before it acts on information it receives.
If you’re using a broadband connection you’ll load pages Much faster now
High CPU and Memory Use? Try This Fix.
1. Remove unwanted Extensions and themes
Extensions and themes can cause Firefox to use more memory than it normally would. Starting Firefox in Firefox Safe Mode and observing its memory usage, will tell you whether extensions and themes are significant memory consumers for you
2. Update Plugins
Older versions of plugins can consume large amounts of memory. You should make sure you're using the latest versions of your plugins.
3. Clear Download History
Firefox can use excessive memory if you have a large download history. The solution is to simply clear your download history.
- At the top of the Firefox windowOn the menu bar, click the Tools menu, and select Clear Private Data.... The Clear Private Data window will open.
- In the Clear Private Data window, select Download History and deselect the other items.
- Click Clear Private Data Now.
4. Configure Firefox Properly
All the following tips can be achieved by typing in about:config in the Firefox address bar.
(I)Browser.cache.memory.capacity-
Controls the maximum amount of memory to use for caching decoded images and chrome (application user interface elements).
This determines if and how much system ram Firefox will use to cache itself. The element does not exist and has to be created. The default value is set to automatic which means that Firefox uses a certain amount of RAM by default. (values for Firefox 2.x)
• 32 MB of RAM -> 2 MB
• 64 MB of RAM -> 4 MB
• 128 MB of RAM -> 6 MB
• 256 MB of RAM -> 10 MB
• 512 MB of RAM -> 14 MB
• 1024 MB of RAM -> 18 MB
• 2048 MB of RAM -> 24 MB
• 4096+ MB of RAM > 32+MB
(II)Browser.sessionhistory.max_entries
o Firefox 2.x saves the last 50 visited websites of a single session in memory which means that it could add up quickly if you visit lots of content filled websites.
o Reduce the amount of websites that are stored this way to reduce the memory consumption. It does not make a huge difference for most surfing habits to reduce the figure to 5 or 10.
(III)Browser.sessionhistory.max_total_viewers
o Automatically determine the maximum amount of pages to store in memory based on the total amount of RAM.
o If you have 64 MB or Ram 1 page is stored in memory, 2 for 128 MB, 3 for 256 MB, 5 for 512 and 8 for everything higher than that figure.
o If you never navigate using the Back and Forward buttons in Firefox you can set this value to 0 to disable the feature.
o Otherwise reduce the amount of pages stored in memory to make this feature use less memory.
(IV)Config.trim_on_minimize
• This preference determines whether to allow Windows to reclaim memory from a minimized Mozilla application.
• Set to True if you want to free up memory when minimizing Firefox.
• The value does not exist by default, simply create it and set it to true for better memory management
Sunday, June 15, 2008
Disabling the internal speaker
Disable Speaker
If you're running Microsoft Windows you can disable the Internal speaker or PC speaker by following the below steps.
Enable Speaker
- Open Device Manager
- In Device Manager click View and click "Show hidden devices"
- This should make "Non-Plug and Play Drivers" visible in Device Manager.
- Expand Non-Plug and Play Drivers by clicking the plus and double-click Beep.
- Within the "Beep properties" window click the Driver tab.
- Under the driver tab if you wish to temporarily disable this device click the Stop button. If you wish to permanently disable this device under the Startup Type select Disabled.
if you wish to temporarily enable this device click the Start button. If you wish to permanently enable this device under the Startup Type select System.
Saturday, May 31, 2008
Google easter eggs
xx-boark
xx-klingon
xx-piglatin
xx-elmer
xx-hacker
google holiday
google circa
elgoog
google easter egg
google mentalplex
google scholar
google suggest
google moms
google heart page
Sunday, April 20, 2008
Worm.Win32.Netsky Removal Process
The following process will help you remove it from your system easily and safely.
Worm.Win32.Netsky Manual Removal Process:
1. Click on the Start Menu button, then click on the Control Panel option, and then Double-click on the Add or Remove Programs icon.
2. Locate Worm.Win32.Netsky and double-click on it to uninstall Worm.Win32.Netsky. Follow the screen step-by-step screen instructions to complete uninstallation of Worm.Win32.Netsky.
3. Restart the computer.
4. When it has completed uninstalling you can close Add or Remove Programs and your Control Panel.
5. Close all programs.
6. Stop Worm.Win32.Netsky process. If you do not know how to stop a running process, click here to read more.
7. Delete the following infected files from your system.
EasyAV.exe
EasyAV
secound_document4.pif
e-mail3.pif
approved_file7.pif
Remove Worm.Win32.Netsky with SmithfraudFix:
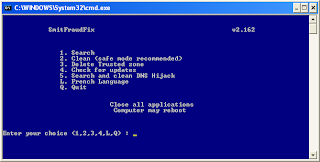
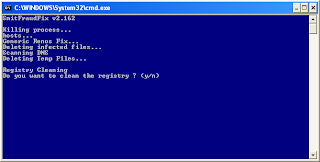
1. Download SmithfraudFix tool and save it to your desktop.
2. Reboot your computer in Safe Mode (before the Windows icon appears, tap the F8 key continually)
3. Double-click SmitfraudFix.exe
4 Select 2 and hit Enter to delete infect files.
5. You will be prompted: Do you want to clean the registry ? answer Y (yes) and hit Enter in order to remove the Desktop background and clean registry keys associated with the infection.
6. The tool will now check if wininet.dll is infected. You may be prompted to replace the infected file (if found): Replace infected file ? answer Y (yes) and hit Enter to restore a clean file.
7. A reboot may be needed to finish the cleaning process. The report can be found at the root of the system drive, usually at C:\rapport.txt
Restore Trusted and Restricted site zone
1. To restore Trusted and Restricted site zone, select 3 and hit Enter.
2. You will be prompted: Restore Trusted Zone ? answer Y (yes) and hit Enter to delete trusted zone.
Search
1. Select 1 and hit Enter to create a report of the infected files. The report can be found at the root of the system drive, usually at C:\rapport.tx
(Disclaimers: These instructions are free and not guaranteed to work. Please use it at your own risks. We are not responsible for any damages.)
Monday, April 14, 2008
How Torrent works - Security
Torrent does not involve any type of active desktop software, unlike other file transfer services such as LimeWire and Napster. There are multitudes of Web sites throughout the Internet where you can search for Torrents. Torrents are active Internet connections that download a specific file you are looking for--referred to in the Torrent network as “seeds.” In order for a seed to be available, someone with the file you are looking for must have the Torrent window open. The Torrent window can either be open when someone is downloading the file for themselves from another seed, or once the file has been downloaded, the Torrent window can remain open to allow other people to download the completed file.
Something that makes Torrent unique is that you are never downloading a single completed file from a single vendor. Instead, you are downloading small segments of data that when put together, create the desired file.
Torrent Security
Torrent is a much safer service than other peer-to-peer networks because of how it functions. While other peer-to-peer services allow a certain degree of access to a shared folder or someone’s hard drive, Torrent users cannot share anything outside of the desired file type that is in an open Torrent window.
Due to the fact that you are only downloading segments of the file as opposed to the full thing, it also makes it incredibly difficult (if not impossible) to transmit viruses through the Torrent system. There are a number of people who are opposed to peer-to-peer technologies because of possible security concerns, however, virtually none of these concerns are found in the Torrent service.
Thursday, March 20, 2008
Remove Win32 AutoRun Worm-Funny UST scandal
Files created by this worm
* x:autorun.inf
* x:xmss.exe
* x:Funny UST Scandal.avi.exe
* %Windir%\autorun.inf
* %Windir%\xmss.exe
* %Windir%\Funny UST Scandal.avi.exe
How to remove
1. Disabled System Restore for Temporary - KB 264887
2. Boot Windows in Safe Mode - KB 315222
3. In Windows Safe Mode, Open Windows Registry Editor
Windows Start > Run > Regedit
Browse to the following registry settings
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\WindowsNT\CurrentVersion\Winlogon\Shell
Replace the value 'explorer.exe, xmss.exe' with 'exporer.exe'
4. Delete all the following files
* C\autorun.inf
* C\xmss.exe
* C\Funny UST Scandal.avi.exe
* X:\autorun.inf
* X:\xmss.exe
* X:\Funny UST Scandal.avi.exe
* %Windir%\autorun.inf
* %Windir%\xmss.exe
* %Windir%\Funny UST Scandal.avi.exe
5. Clean All Windows Temporary Files
6. Restart the Windows
** edit registry values with false data can damage your OS **
Friday, March 14, 2008
Diiferent Type of Security Threats
Viruses, worms, Trojan horses - Your computer files can be destroyed; hackers can gain control over your computer, and viruses can quickly spread to other computers
Hackers - Hackers can access your PC
without your knowledge to steal your private data or use your computer for their own purposes
Identity thieves - Thieves can steal your credit-card number, banking passwords, and more, costing you thousands of dollars
Phishing scams - Replying to a phishing scam can cause you to unknowingly provide criminals with your personal inancial information
Sexual predators - Minors providing strangers with too much personal information in chat rooms, IM sessions, and elsewhere
Privacy intrusions - Marketers and others can learn about your online habits, subjecting you to more pop-ups, identity theft is a possibility
Spam - Your inbox ills up with useless, annoying, even pornographic junk e-mail messages
Instant messaging monitoring & spam - Outsiders can spy on your conversations, send spam and more
Wireless network hackers - Hackers can log your keystrokes, steal your private data, direct you to fraudulent Web sites, and more
Friday, March 7, 2008
Klite codec - codec List for V3.8.0
Contents of version 3.8.0:
Player:
* Media Player Classic [version 6.4.9.1 rev. 40]
ffdshow:
* ffdshow [revision 1872]
* ffdshow VFW interface
* extra plugins
DirectShow video decoding filters:
* XviD [version 1.2.0-dev build 2008-01-10]
* DivX [version 6.8.0.0]
* On2 VP6 [version 6.4.2.0]
* On2 VP7 [version 7.0.10.0]
* MPEG-2 (Cyberlink) [version 8.1.0.1317]
* MPEG-2 (Gabest) [version 1.0.0.4]
* MPEG-1 (MainConcept) [version 1.0.0.78]
DirectShow audio decoding filters:
* AC3/DTS/LPCM/MP1/MP2 (AC3Filter) [version 1.46]
* Vorbis (CoreVorbis) [version 1.1.0.79]
* AAC (CoreAAC) [version 1.2.0.575]
DirectShow audio parsers:
* MusePack (MONOGRAM) [version 0.9.1.2 | 0.3.1.2]
* WavPack (CoreWavPack) [version 1.1.1]
* FLAC (madFLAC) [version 1.7]
* Monkey's Audio (DCoder) [version 1.0]
* OptimFROG (RadLight) [version 1.0.0.1]
* DC-Bass Source [version 1.1.0.0]
* AC3/DTS Source (AC3File) [version 0.5b]
* AMR (MONOGRAM) [version 0.9.0.1]
DirectShow source filters:
* AVI splitter (Gabest) [version 1.0.0.9]
* AVI splitter (Haali Media Splitter) [version 1.7.401.3]
* MP4 splitter (Haali Media Splitter) [version 1.7.401.3]
* MP4 splitter (Gabest) [version 1.0.0.4]
* Matroska splitter (Haali Media Splitter) [version 1.7.401.3]
* Matroska splitter (Gabest) [version 1.0.3.0]
* Ogg splitter (Haali Media Splitter) [version 1.7.401.3]
* Ogg splitter (Gabest) [version 1.0.0.1]
* MPEG PS/TS splitter (Gabest) [version 1.0.0.4]
* MPEG PS/TS splitter (Haali Media Splitter) [version 1.7.401.3]
* FLV splitter (Gabest) [version 1.0.0.4]
* CDDA Reader (Gabest) [version 1.0.0.2]
* CDXA Reader (Gabest) [version 1.0.0.2]
DirectShow subtitle filter:
* DirectVobSub (a.k.a. VSFilter) [version 2.38]
* DirectVobSub (a.k.a. VSFilter) [version 2.33]
Other filters:
* Haali Video Renderer [version 1.7.401.3]
VFW video codecs:
* XviD [version 1.2.0-dev build 2008-01-10]
* DivX Pro [version 6.8.0.14]
* x264 [revision 736bm]
* On2 VP6 [version 6.4.2.0]
* On2 VP7 [version 7.0.10.0]
* Intel Indeo 4 [version 4.51.16.2]
* Intel Indeo 5 [version 5.2562.15.54]
* Intel I.263 [version 2.55.1.16]
* huffyuv [version 2.1.1 CCE Patch 0.2.5]
* I420 (Helix) [version 1.2]
* YV12 (Helix) [version 1.2]
ACM audio codecs:
* MP3 (Fraunhofer) [version 3.4.0.0]
* MP3 (LAME) [version 3.97]
* AC3ACM [version 1.4]
* Vorbis [version 0.0.3.6]
* DivX ;) Audio [version 4.2.0.0]
Tools:
* Codec Tweak Tool [version 2.2.5]
* GSpot Codec Information Appliance [version 2.70a]
* MediaInfo Lite [version 0.7.5.9]
* VobSubStrip [version 0.11]
* GraphEdit [build 061102]
* Haali Muxer [version 1.7.359.22]
* FourCC Changer
* Bitrate Calculator
Saturday, February 16, 2008
NTFS vs FAT
Criteria | NTFS5 | NTFS | FAT32 | FAT16 | FAT12 |
| Operting System | Windows 2000 | Windows NT | DOS v7 and higher | DOS | DOS |
|
| |||||
| Limitations | |||||
| Max Volume Size | 2TB | 2TB | 32GB for all OS. | 2GB for all OS. | 16MB |
| Max Files on Volume | Nearly Unlimited | Nearly Unlimited | 4194304 | 65536 | |
| Max File Size | Limit Only by | Limit Only by | 4GB minus 2 Bytes | 2GB (Limit Only | 16MB (Limit Only |
| Max Clusters Number | Nearly Unlimited | Nearly Unlimited | 4177918 | 65520 | 4080 |
| Max File Name Length | Up to 255 | Up to 255 | Up to 255 | Standard - 8.3 | Up to 254 |
|
| |||||
| File System Features | |||||
| Unicode File Names | Unicode Character Set | Unicode Character Set | System Character Set | System Character Set | System Character Set |
| System Records Mirror | MFT Mirror File | MFT Mirror File | Second Copy of FAT | Second Copy of FAT | Second Copy of FAT |
| Boot Sector Location | First and Last Sectors | First and Last Sectors | First Sector and | First Sector | First Sector |
| File Attributes | Standard and Custom | Standard and Custom | Standard Set | Standard Set | Standard Set |
| Alternate Streams | Yes | Yes | No | No | No |
| Compression | Yes | Yes | No | No | No |
| Encryption | Yes | No | No | No | No |
| Object Permissions | Yes | Yes | No | No | No |
| Disk Quotas | Yes | No | No | No | No |
| Sparse Files | Yes | No | No | No | No |
| Reparse Points | Yes | No | No | No | No |
| Volume Mount Points | Yes | No | No | No | No |
|
| |||||
| Overall Performance | |||||
| Built-In Security | Yes | Yes | No | No | No |
| Recoverability | Yes | Yes | No | No | No |
| Performance | Low on small volumes | Low on small volumes | High on small volumes | Highest on small volumes | High |
| Disk Space Economy | Max | Max | Average | Minimal on large volumes | Max |
| Fault Tolerance | Max | Max | Minimal | Average | Average |
|
|
|
|
|
| |
|
|
|
|
|
| |
Enable / Disable Task Manager in Windows XP
- Click Start
- Click Run
- Enter gpedit.msc in the Open box and click OK
- In the Group Policy settings window
- Select User Configuration
- Select Administrative Templates
- Select System
- Select Ctrl+Alt+Delete options
- Select Remove Task Manager
- Double-click the Remove Task Manager option
Hive: HKEY_CURRENT_USER
Key: Software\Microsoft\Windows\CurrentVersion\Policies\System
Name: DisableTaskMgr
Type: REG_DWORD
Value: 1=Enablethis key, that is DISABLE TaskManager
Value: 0=Disablethis key, that is Don't Disable, Enable TaskManager
Friday, January 18, 2008
Common Virus Folders and Files
%System%\IEXPLORE.EXE,
%System%\EXPLORE.EXE,
%Windir%\rundll32.exe,
%System%\userinit32.exe,
%system32%,
X:\Documents and Settings\XXXX\Local Settings\Temp,
autorun.inf,
desktop.ini
some virus have similar windows file names, like scvhost.exe, rundl32.exe, crss.exe, lsuss.exe etc
Tuesday, January 15, 2008
How to block Email Virus
Email virus are found in attachments, always check your attachments before u open it
be careful while opening these file formats
File Extension | File type |
|---|---|
| .ade | Microsoft Access project extension |
| .adp | Microsoft Access project |
| .bas | Microsoft Visual Basic class module |
| .bat | Batch file |
| .chm | Compiled HTML Help file |
| .cmd | Microsoft Windows NT Command Script |
| .com | Microsoft MS-DOS program |
| .cpl | Control Panel extension |
| .crt | Security certificate |
| .exe | Program |
| .hlp | Help file |
| .hta | HTML program |
| .inf | Setup Information |
| .ins | Internet Naming Service |
| .isp | Internet Communication settings |
| .js | JScript file |
| .jse | Jscript Encoded Script file |
| .lnk | Shortcut |
| .mda | Microsoft Access add-in program |
| .mdb | Microsoft Access program |
| .mde | Microsoft Access MDE database |
| .mdz | Microsoft Access wizard program |
| .msc | Microsoft Common Console Document |
| .msi | Microsoft Windows Installer package |
| .msp | Windows Installer patch |
| .mst | Visual Test source files |
| .pcd | Photo CD image or Microsoft Visual Test compiled script |
| .pif | Shortcut to MS-DOS program |
| .reg | Registration entries |
| .scr | Screen saver |
| .sct | Windows Script Component |
| .shs | Shell Scrap Object |
| .url | Internet shortcut |
| .vb | VBScript file |
| .vbe | VBScript Encoded Script file |
| .vbs | VBScript file |
| .wsc | Windows Script Component |
| .wsf | Windows Script file |
| .wsh | Windows Script Host Settings file |
and always download attachments mailed by known senders
if you are using any email client softwares like outlook, thunder bird etc
configure your anti virus for your email clients software and update your email software frequently .
Saturday, January 12, 2008
GMail Adds Group Mailing List Functions
Wednesday, January 2, 2008
Movie player 4 linux
To install MPlayer from source code, download the code tarball. Extract the files into a temporary directory. Change to the directory into which you downloaded the files and enter the following commands:
./configure --enable-gui
make
su (if you're not already root)
make install
















